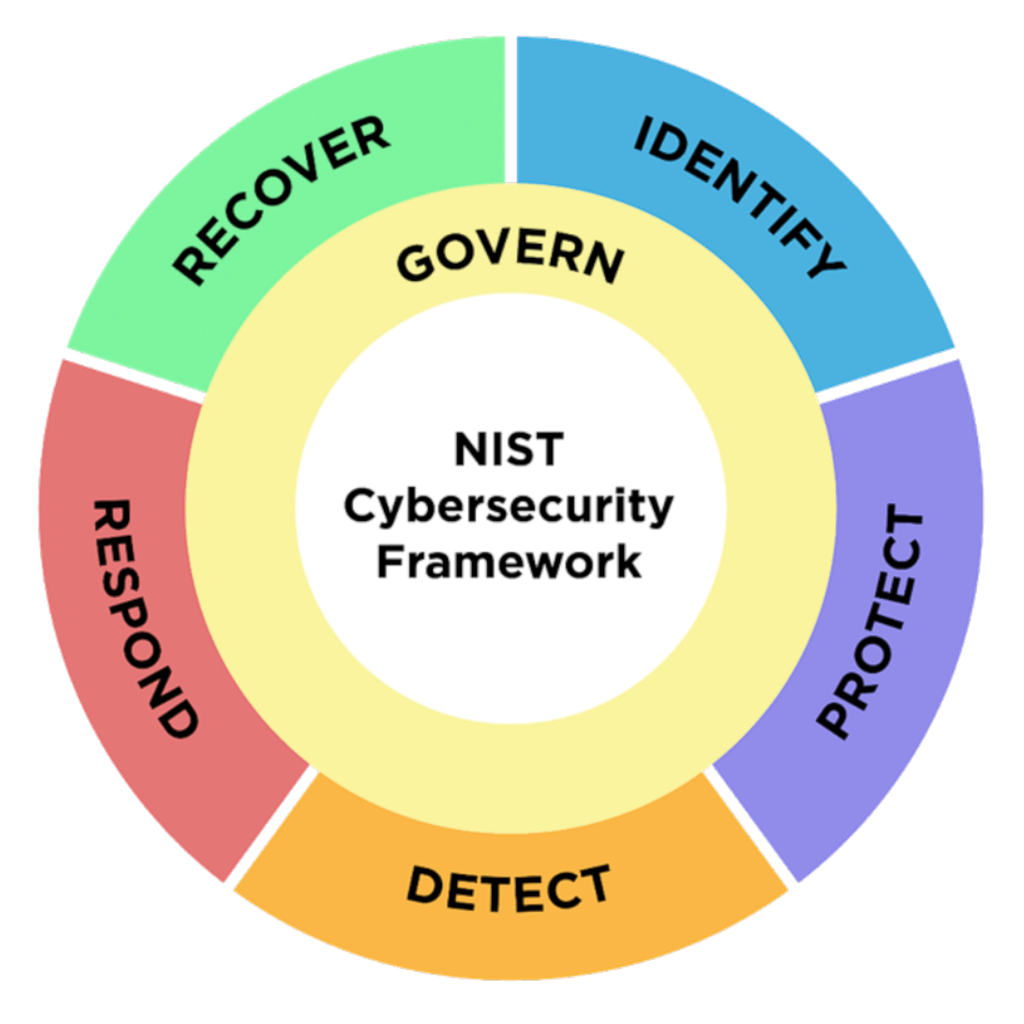
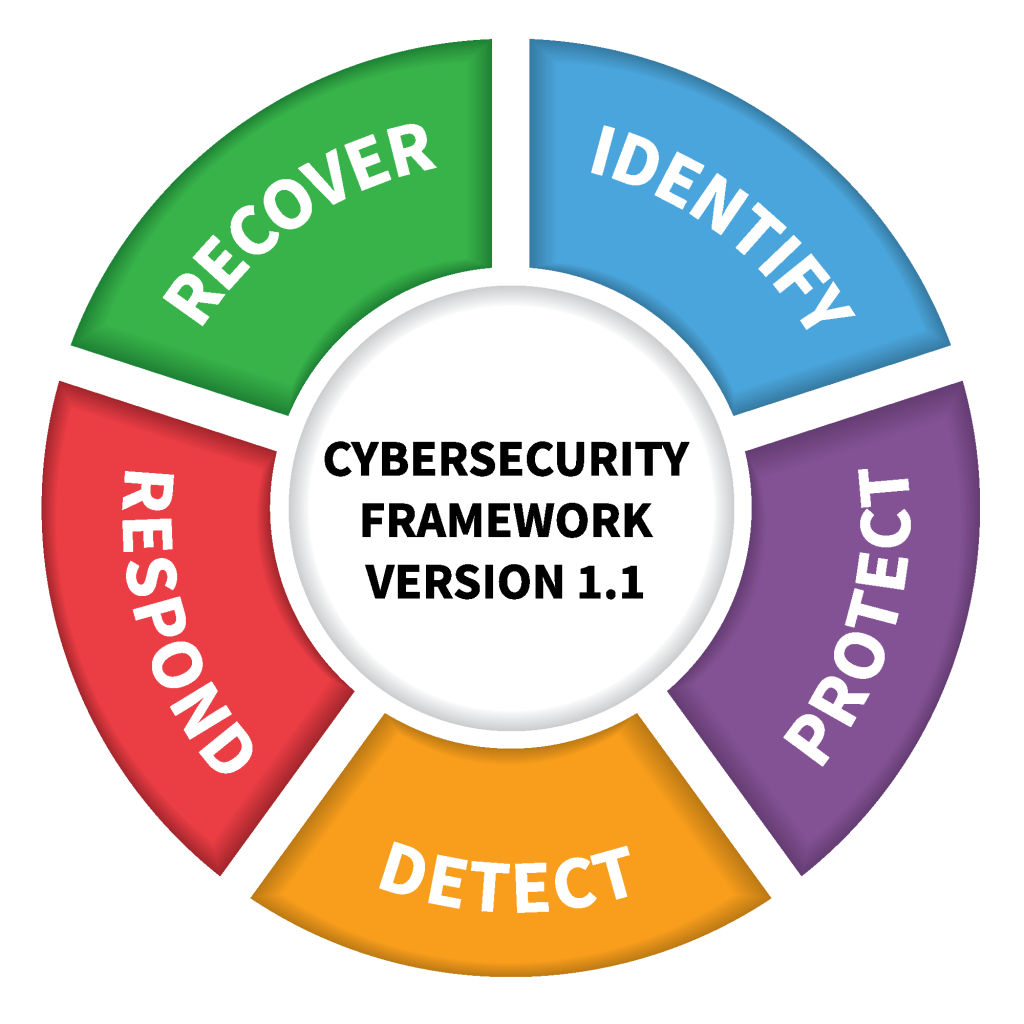
The NIST CSF is getting a major update for first time since it was released in 2014. With the addition of a GOVERN as new function, NIST hopes this will encourage more users to adopt the framework.
But why? In brief, everyone uses the internet differently.
Historically, the internet arose from research and development commissioned in the 1970s by the Defense Advanced Research Projects Agency (DARPA) of the United States Department of Defense in collaboration with universities and researchers across the United States, the United Kingdom, and France.
The internet has come a long way since ARPANET. Many developing countries are just starting to connect to the internet in a meaningful way. This influx of new users is tearing holes in the security infrastructure of the internet. Everyday, bad actors across the world are finding new ways to exploit any weakness they can find. By making the knowledge and tools easily accessible, understandable, and standardized, The NIST Cybersecurity Framework aims to make a better, safer internet for all.
NIST CSF Framework
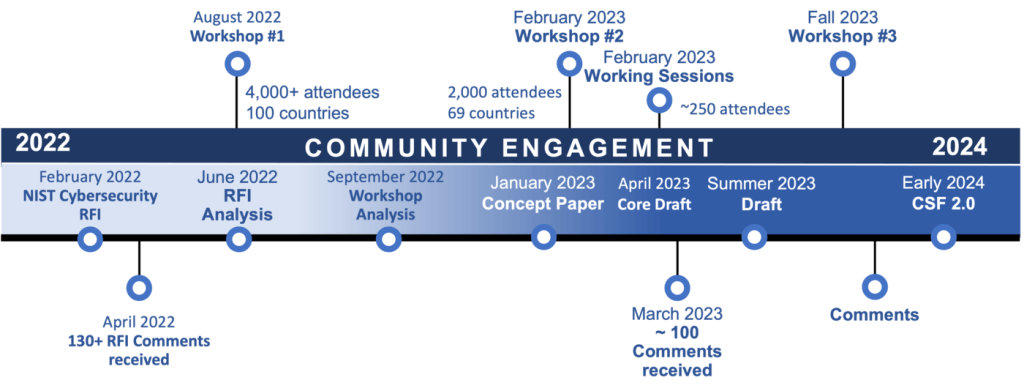
NIST CSF 2.0 Draft Framework Timeline
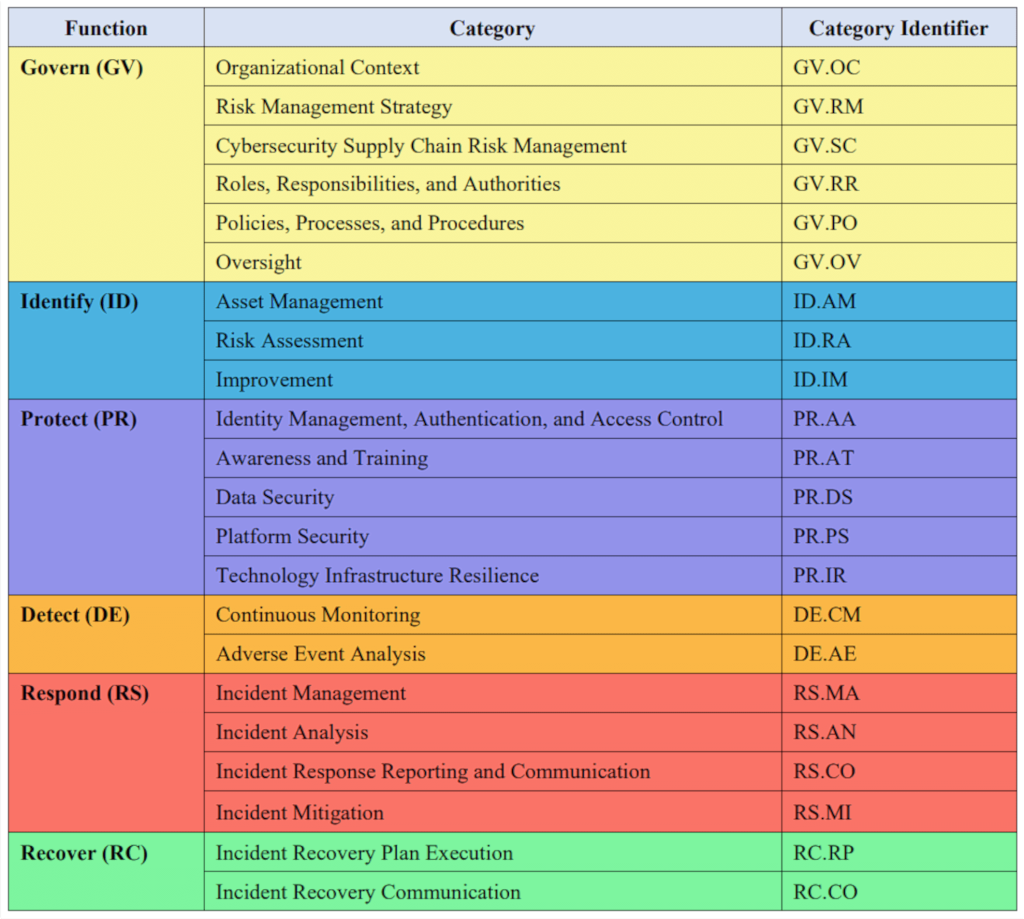
CSF 2.0 Core Function and Category Names and Identifiers
Functions, Categories, and Subcategories
The Framework Core Functions — GOVERN, IDENTIFY, PROTECT, DETECT, RESPOND, and RECOVER — organize cybersecurity outcomes at their highest level
- GOVERN (GV) – Establish and monitor the organization’s cybersecurity risk management strategy, expectations, and policy. The GOVERN Function is cross-cutting and provides outcomes to inform how an organization will achieve and prioritize the outcomes of the other five Functions in the context of its mission and stakeholder expectations. Governance activities are critical for incorporating cybersecurity into an organization’s broader enterprise risk management strategy. GOVERN directs an understanding of organizational context; the establishment of cybersecurity strategy and cybersecurity supply chain risk management; roles, responsibilities, and authorities; policies, processes, and procedures; and the oversight of cybersecurity strategy.
- IDENTIFY (ID) – Help determine the current cybersecurity risk to the organization. Understanding its assets (e.g., data, hardware, software, systems, facilities, services, people) and the related cybersecurity risks enables an organization to focus and prioritize its efforts in a manner consistent with its risk management strategy and the mission needs identified under GOVERN. This Function also includes the identification of improvements needed for the organization’s policies, processes, procedures, and practices supporting cybersecurity risk management to inform efforts under all six Functions.
- PROTECT (PR) – Use safeguards to prevent or reduce cybersecurity risk. Once assets and risks are identified and prioritized, PROTECT supports the ability to secure those assets to prevent or lower the likelihood and impact of adverse cybersecurity events. Outcomes covered by this Function include awareness and training; data security; identity management, authentication, and access control; platform security (i.e., securing the hardware, software, and services of physical and virtual platforms); and the resilience of technology infrastructure.
- DETECT (DE) – Find and analyze possible cybersecurity attacks and compromises. DETECT enables timely discovery and analysis of anomalies, indicators of compromise, and other potentially adverse cybersecurity events that may indicate that cybersecurity attacks and incidents are occurring.
- RESPOND (RS) – Take action regarding a detected cybersecurity incident. RESPOND supports the ability to contain the impact of cybersecurity incidents. Outcomes within this Function cover incident management, analysis, mitigation, reporting, and communication.
- RECOVER (RC) – Restore assets and operations that were impacted by a cybersecurity incident. RECOVER supports timely restoration of normal operations to reduce the impact of cybersecurity incidents and enable appropriate communication during recovery efforts.
How To Use The NIST CSF
- Define the use case for the Profiles. The use case defines the high-level facts and assumptions on which the Profiles will be based, as a way of scoping the Profiles. This can include:
- The reason for creating the Profiles
- The organization’s divisions, information and technology assets, services, and other elements that are in scope for these Profiles
- Those who will develop, review, and operationalize the Profiles
- The individuals who will set expectations for actions to achieve the cybersecurity outcomes
- Gather the information needed to prepare the Profiles. An organization can gather relevant resources prior to preparing the Profiles, such as organizational policies, risk management priorities and resources, cybersecurity requirements and standards followed by the organization, and work roles. Understanding cybersecurity governance — such as identifying the organization’s mission, its stakeholders, and their needs and expectations, as outlined in the GOVERN Function — is generally needed for preparing a Target Profile.
- Create Current and Target Profiles. Determine what types of supporting information (also known as elements) each Profile should include for each of the selected Framework outcomes, and fill in the elements for each selected outcome. Consider the risk implications of the current state to inform target state planning and prioritization. Appendix A provides a notional template for Current and Target Profiles and examples of common elements that organizations can choose to use. Examples of elements in a Profile for each outcome Category or Subcategory include the outcome’s priority compared to other outcomes; current status in achieving the outcome; policies, processes, and procedures; practices, including tools and responsibilities; metrics and measurements; informative references; and any other supporting information that an organization considers helpful. Organizations documenting responsibilities may employ the Workforce Framework for Cybersecurity (NICE Framework), which provides a common lexicon for describing cybersecurity work.
- Analyze the Profiles and create an action plan. Identifying and analyzing the differences between the Current and Target Profiles enables an organization to identify gaps and develop a prioritized action plan for addressing those gaps to improve cybersecurity. This plan should consider mission drivers, benefits, risks, and necessary resources (e.g., staffing, funding). Using Profiles in this manner helps an organization make better-informed decisions about how to improve cybersecurity risk management in a cost-effective manner. Appendix A provides a notional action plan template.
- Implement the action plan and update the Profiles. The organization follows the action plan to adjust its cybersecurity practices to address gaps and move toward the Target Profile. Improving an organization’s cybersecurity program is a continuous effort, and implementing an action plan can take months or years. At frequencies defined by the organization, the Current Profile should be updated to assess progress and the Target Profile should be updated to reflect changes in the organization and its cybersecurity risk.
NIST CSF 2.0 – IDENTIFY Example
Links:
NIST Cybersecurity Framework Home Page
Discussion Draft: NIST CSF 2.0 Core with Implementation Examples PDF
April 24, 2023 – Discussion Draft: NIST Cybersecurity Framework 2.0 PDF
August 08, 2023 – Public Draft: NIST Cybersecurity Framework 2.0 PDF
